As an IT practitioner, security is never far from your mind. In fact, in a recent JumpCloud survey, 60% of IT professionals working at small- to medium-sized enterprises (SMEs) said security was their biggest challenge.
Among the myriad of influencing factors, shadow IT has emerged as a formidable adversary: 84% of IT professionals said they are concerned about shadow IT. 29% listed it as one of their top three security concerns.
However, eliminating shadow IT is easier said than done, and in many organizations, shadow IT remains unaddressed.This blog will cover the looming challenge of shadow IT, including why it’s such a challenge and what makes it so hard to eliminate.
Unless otherwise cited, all info cited in this article comes from JumpCloud’s industry report, Detours Ahead: How IT Navigates an Evolving World.
Shadow IT Is a Prolific Challenge
Shadow IT is the use of applications or tools by employees without the explicit knowledge or approval of the IT department. While we often think of threats as malicious, this threat often comes with the best intentions: often, shadow IT stems from employees looking for better ways to do their work.
This occurs increasingly often as SaaS tools become more specialized and easier for the layperson to adopt. Gone are the days of the monolith Microsoft suite — workplaces are filled with dozens (perhaps hundreds) of niche tools, from social media trackers to flowchart creators to personal project management tools. They’re user-friendly, easy to sign up for, and often, free. It’s no wonder users are adopting them left and right.
While these tools can often boost productivity and streamline processes, they introduce significant security vulnerabilities. For one, shadow resources are not registered with or monitored by the IT department, which means they don’t adhere to the company’s established security protocols. This increases the risk of cyberattacks, data breaches, and noncompliance with regulations and governance policies. Further, because IT can’t view or monitor these resources, the IT team is unable to detect or respond to threats and attacks in a timely manner, which gives attackers more time to infiltrate systems undetected.
So… Why Not Address It?
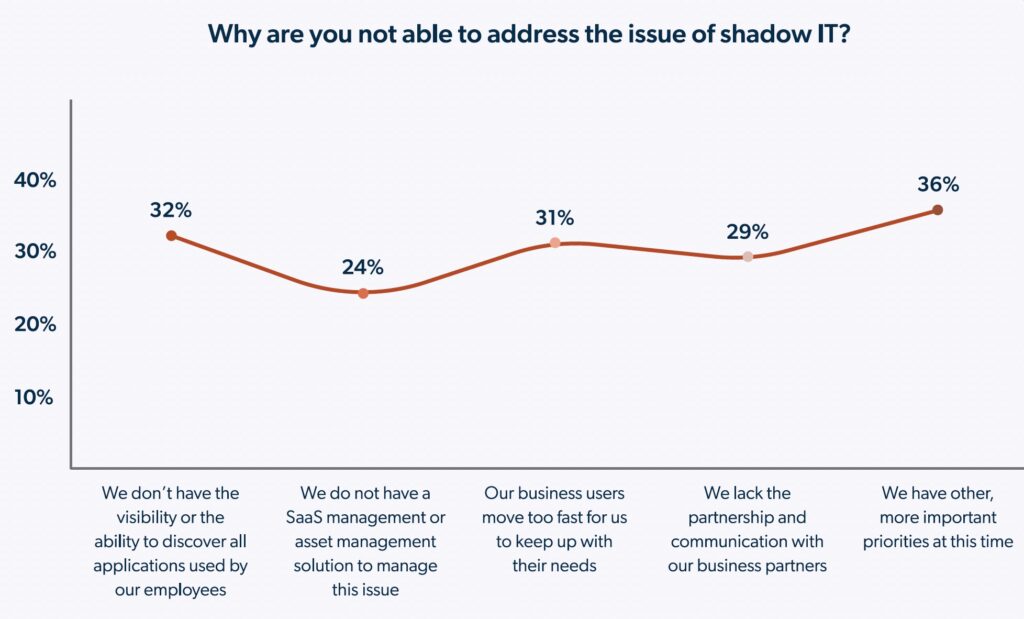
Despite the high risk and levels of concern associated with shadow IT, eradicating it is easier said than done. IT professionals cited several reasons that shadow IT continues to proliferate in their environments, from other issues taking higher priority to IT teams feeling ill-equipped to identify all the applications being utilized by employees.
IT Sprawl Is Like a High School Party (Stay with Us Here)
IT sprawl plays a major role in the rise of shadow IT. It’s easy for SME environments to become sprawled: fast decision making, the need for many new tools during growth periods, and a lack of centralized tool management make IT sprawl a common problem. But IT sprawl is a hard thing to face, and a harder thing to think about eliminating.
IT sprawl is like a monstrous pile of junk you’ve stuffed into a closet. A classic high school party guest list that’s gotten out of control. A project you’ve taken way too far in the wrong direction and don’t know how to bring it back. It just keeps getting bigger and messier. The easiest thing to do is to not look at it.
Most IT teams are juggling a lot of competing priorities with very little extra time to spend on them. So, all too often, the result is to ignore it and focus on other problems at hand.
But, like our closet mess or high school guest list, the longer it goes unaddressed, the worse the problem gets. In IT sprawl’s case, your architecture gets increasingly complex, with your teams managing more and more disparate tools with questionable integrations. You end up IT reacting to problems far more often than you’re able to prevent them. And with multiple teams using different solutions, it becomes challenging to have a clear view of what’s being used across the organization.
While stepping back and looking at the mess can be intimidating, the security and operational implications of not doing so are far scarier.
Fortunately, there’s a solution to this snowball of a problem.
Unified IT Management: A Solution in Sight
Amidst these challenges, a silver lining emerges: unified IT management is gaining traction as a viable solution. Unifying your environment helps wrangle IT sprawl and makes it easier to spot and address shadow IT. The majority of IT professionals favor unified IT: 84% said they would prefer a single platform to manage user identity, access, and security over a mix of best-in-class point solutions.
Unified IT doesn’t have to mean getting rid of the tried and true tools you already rely on. The key is to look for a solution that can do two things:
- Unify several of the disparate tools you use now.
- Integrate with your existing architecture.
By using tools that play nice with your current infrastructure, you can chart a course toward unification without calling the cops on your own party, so to speak. No need to immediately trash everything you’re working with — instead, you can introduce the new solution and transition toward it in stages, peeling away old layers without breaking things or disrupting your environment.
More on Shadow IT
Now that you know why shadow IT is so hard to eliminate, expand your knowledge by uncovering the 6 key risks that shadow IT can create for your organization and the main forms of shadow IT you need to watch out for. Grab a copy of the free eBook, Casting IT into the Shadows, to learn more.





