Editor’s note: this article is meant to be a helpful guide for Linux administrators and enthusiasts, and does not necessarily imply direct coverage within the JumpCloud Directory Platform. While JumpCloud has a wide array of features that support multiple Linux distributions, we recommend looking at our compatibility matrix to ensure adequate coverage for the distributions you support.
Encryption is considered to be a fundamental aspect of securing data. For Linux users, especially those using popular distributions such as Ubuntu, Debian, RedHat, Fedora, or others, selecting the appropriate encryption tools can significantly impact the security and performance of their system. We will comprehensively analyze existing and mostly used encryption tools available for these distributions so that we can explore features, strengths, and weaknesses.
Before providing different encryption tools, we need to understand the basic concepts of encryption. Encryption is the process of converting data into code to prevent unauthorized access. It is achieved by using algorithms that transform the original information which is in plain text format into an unreadable format or ciphertext. There are multiple approaches to encryption and also the security itself depends on the strength of the algorithm and the secrecy of the key that is used to encrypt and decrypt the data.
Key Types of Encryption
- Symmetric Encryption: Uses the same key for both encryption and decryption. This type of encryption includes AES (Advanced Encryption Standard) and DES (Data Encryption Standard)
- Asymmetric Encryption: This type utilizes a pair of keys, where a public key is used for encryption and a private key for decryption. Examples are RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography).
Different Types of Encryption Tools for Linux
Several encryption tools can be used in Linux, and each of these has its unique features and use cases. They also come with pros and cons. We will focus on the following tools:
- GnuPG (GPG)
- dm-crypt/LUKS
- EncFS
- eCryptfs
- VeraCrypt
GNUPG (GPG)
GnuPG, or GPG is an open-source implementation of the OpenGPG standard. It is mainly used when encrypting files and communications, offering both symmetric and asymmetric encryption. It works across multiple Linux distributions, there is a proper key management where we can generate, sign, or revoke a key. It supports both file encryption and email encryption. The only drawback is that can be challenging for beginners due to the command line interface and also complex key management.
Let’s try to generate a GPG key pair, encrypt a file, and then decrypt it. In this example, we will use the latest Ubuntu 24.04 version.
GPG is already installed on Ubuntu by default, so the next step is to generate a GPG key pair with the following command:
gpg ––full-generate-key
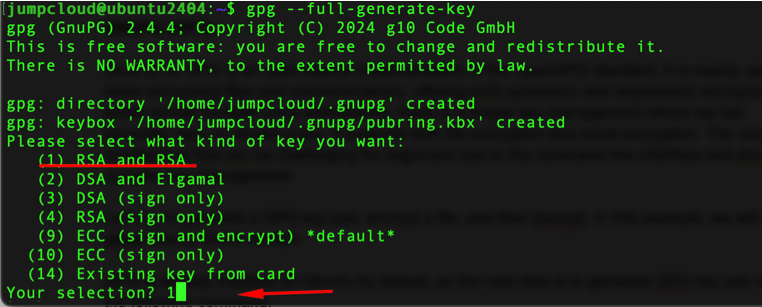
Choose the default setting under number 1, which is RSA and RSA.
Next, select the key size, where the 2048-bit setting is fine but the 4096-bit setting is more secure.
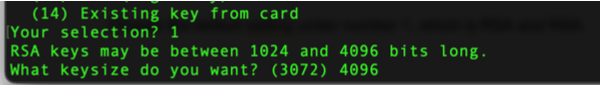
The following prompt will ask us about the key expiration, so we can choose for how long you want the key to be valid. For this example, we can choose 0 for no expiration. To increase the security of your files and information, consider placing proper expiration.
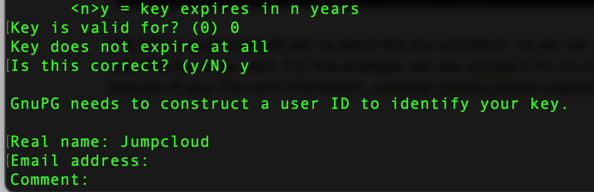
The next prompt is where we can add the real name, email address, and potential comment. These fields are not mandatory and at the bottom of the prompt, you can press O and Enter.
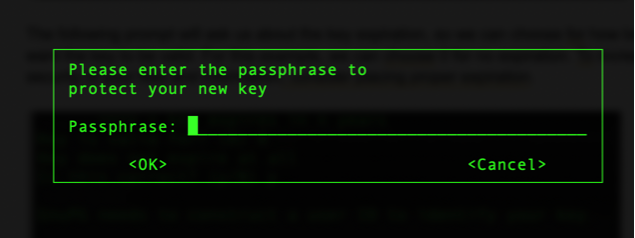
Now we need to enter the passphrase so we can protect our key. Make sure to place complex passwords and combinations of letters (both uppercase and lowercase), numbers, and special characters.
After the process, you will get a similar output:
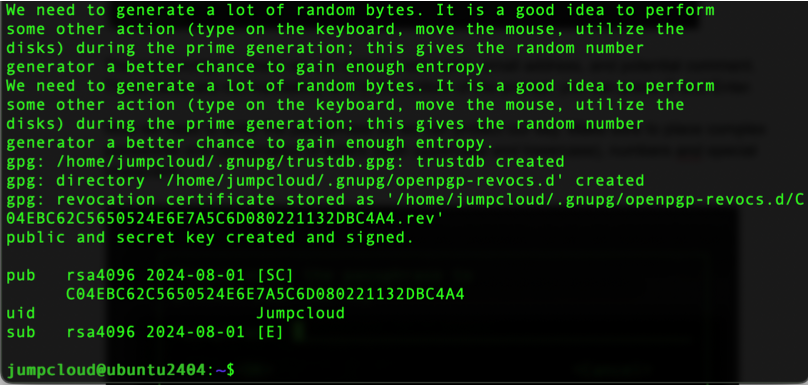
Now we can first create a sample file and encrypt it with our newly generated GPG key:
echo “This is a secret message” > secret.txt
gpg ––encrypt -r jumpcloud secret.txt
Make sure to change the command according to your user ID.
If we list the directory we will see that a new file has been created with the extension .gpg
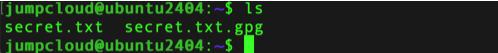
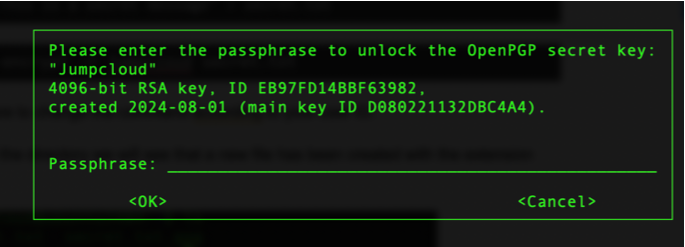
Now, we can decrypt our file by running the following command. Also, we will be prompted for the passphrase that we set up earlier.
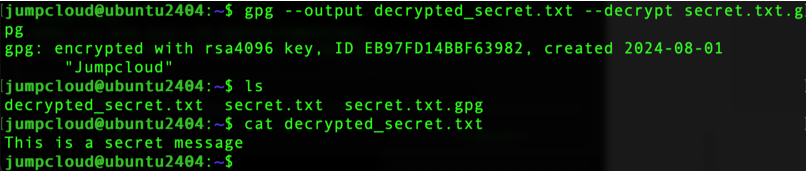
gpg ––output decrypted_secret.txt ––decrypt secret.txt.gpg
After the decryption process, we can see that the contents of our file are the same as the one we encrypted.
dm-crypt/LUKS
Dm-crypt and LUKS are often mentioned together because they are complementary components used for disk encryption in Linux. Dm-crypt is a kernel-level disk encryption sub-system which a part of the Linux device mapper, and it can encrypt entire disks or partitions. Since it’s a part of the Linux kernel, this means that it offers highly efficient encryption while supporting various encryption algorithms and key sizes.
LUKS (Linux Unified Key Setup) is a standard for disk encryption and it is primarily designed to simplify the usage of dm-crypt. It provides a standardized on-disk format that ensures proper compatibility while simplifying the process of setting up and managing encrypted partitions. It also supports multiple passphrases, which allows easier key management and recovery.
In this process, when you configure the disk encryption you use tools like “cryptsetup” tool which will initialize LUKS on the partition and manage it. We have articles that cover the entire process of encryption with LUKS.
EncFS
EncFS is an encryption tool where it runs without any kernel-level modifications. This type of encryption will encrypt individual files rather than entire partitions, and it is simple to set up and use for beginners. The drawback is that it is slightly slower than kernel-based encryption methods due to user-space operation. There is also a concern about the strength of its encryption compared to other tools.
If you try to install it on the latest version of Ubuntu, you will receive the following information:
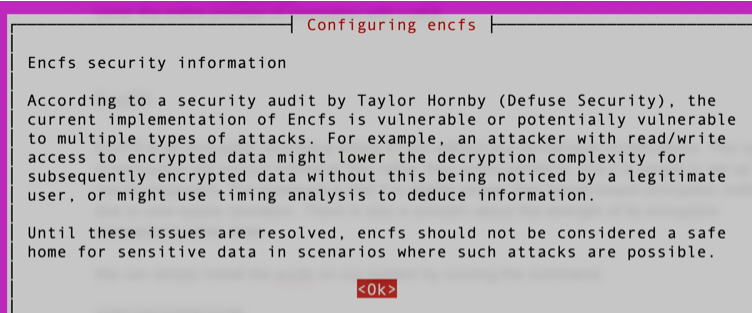
eCryptfs
eCryptfs is a stacked cryptographic file system that allows you to encrypt certain directories. This tool will automatically encrypt and decrypt files as they are accessed. When it comes to integration, they are built into the Linux kernel, which ensures compatibility and performance. It is easy to use and generally, it has good performance due to kernel-level integration. One of the drawbacks is less flexibility regarding encryption options and configurations. There is also limited community support compared to other tools.
We can start by installing the utilities needed for this tool:
sudo apt install ecryptfs-utils
Next, we can create two directories, one for the encrypted data and one for the mount point.
mkdir ~/encrypted_data
mkdir ~/decrypted_data
Now, we can mount the “encrypted_data” directory to “decrypted_data” using eCryptfs:
sudo mount -t ecryptfs ~/encrypted_data ~/decrypted_data
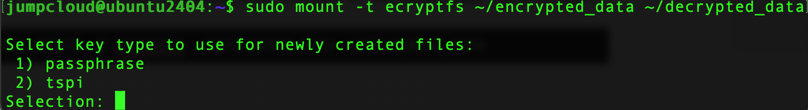
We will be prompted to enter our preferred option, in our case we will use the passphrase. So, press 1 and press Enter.
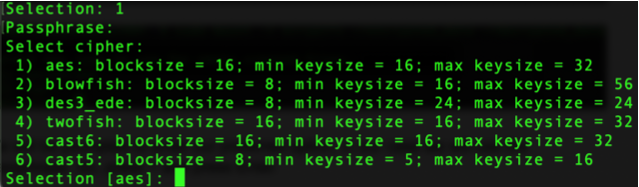
We can also proceed with the default value of aes, select the keysize to 32, and type n for the Plaintext Passthrough option, since in that case files written to the eCryptfs mount point are not automatically encrypted. This can be useful for debugging and testing purposes, but make sure to disable this option in production environments.
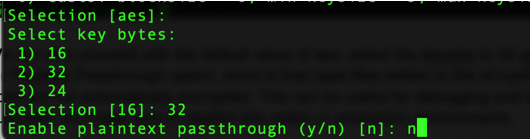
In this process, we will also enable filename encryption:
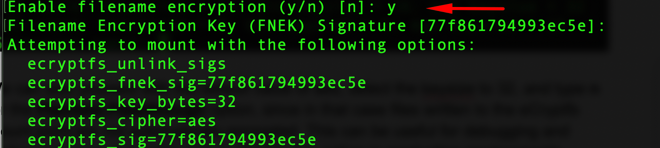
We can now use the “decrypted_data” directory as we would use any directory in our system. The files in this directory will be encrypted and stored in the “encrypted_data” directory.
Next, we can create a file in the decrypted directory.
echo “This is a secret message” > ~/decrypted_data/secret.txt
We can verify that the file is encrypted if we check the contents of our “encrypted_data” directory.
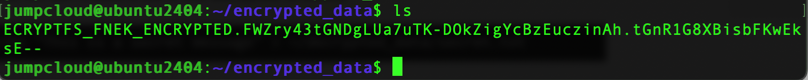
VeraCrypt
VeraCrypt is a popular open-source disk encryption tool that is derived from TrueCrypt. It can offer both full-disk encryption and virtual encrypted disks. It is available for different operating systems such as Linux, MacOS, and Windows. VeraCrypt also supports the creation of hidden volumes for increased security. It comes both with GUI as well as command-line options. Some of the drawbacks are slightly higher overhead when compared to native Linux tools and some advanced features can be complex to configure.
Comparing Encryption Tools Across Linux Distributions
Different Linux distributions (and their communities) may favor one tool over another. The same goes for compatibility, default configurations, and package management. Here is a breakdown of encryption tools for popular distributions.
Ubuntu and other Debian-based distributions
- GnuPG: Essential part of the system, used for package signing and more.
- dm-crypt/LUKS: Supported with extensive documentation where tools like “cryptsetup” are readily available.
- EncFS: It is available in the repositories but due to security issues, it is not the preferred tool to use.
- eCryptFS: Commonly used for home directory encryption; it’s not pre-configured and may require a manual setup for Debian.
- VeraCrypt: This tool is available for installation through third-party repositories, and the basic setup is relatively easy to use.
Redhat, Fedora, and other RHEL derivatives
- GnuPG: Mainly used for securing communications and package signing.
- dm-crypt/LUKS: It’s a preferred method of disk encryption and it also has enterprise-level support for RedHat. Cryptsetup is readily available, similar to Debian-based distributions.
- EncFS: It is available for installation, however, it is not preferred or recommended for enterprise environments due to security issues.
- eCryptFS: Supported, with good documentation and community support. It is less used compared to dm-crypt/LUKS.
- Veracrypt: Available through third-party repositories but it’s less commonly used in enterprise environments. It is directly supported by Fedora.
Choosing the Right Encryption Tool
Selecting the right encryption tool for your Linux operating system ultimately depends on your needs and the distribution you are using.
We can recommend dm-crypt/LUKS for full-disk encryption across all distributions. It is a great choice that offers strong security and it doesn’t affect the performance of your system.
When you need to encrypt specific files or directories, tools like GnuPG and eCryptFS provide enough protection as well as flexibility and ease of use. EncFS can be used for testing, but we are not recommending it for production environments. VeraCrypt is also a good choice for users who work across different operating systems and GUI can help with the configuration.
Choosing the exact encryption also depends on the requirements for your use case, security requirements, technical proficiency, and specific demands of your Linux distribution. By understanding the features and capabilities of each tool you can make an informed decision.
JumpCloud offers a wide range of management capabilities to support Linux systems across many different distros and versions. If you haven’t seen them yet, head to our Help Center where you can see what versions of Linux we support as well as guides on important topics like configuring settings for Linux policies, setting up patching schedules, and (of course) configuring data encryption on Linux devices.
If you’re the hands-on type, start a no-obligation free trial today.




