JumpCloud’s System Insights extends device management by providing telemetry across your fleet of macOS, Windows, and Linux devices. You can easily gather information from JumpCloud-managed devices with our RESTful API and PowerShell Module.
You can use the System Insights feature to:
- Easily take stock of your suite of devices and the state of the machines in your organization.
- See inventory information like vendor, model, serial number, etc.
- Query device endpoints to proactively resolve issues without having to interrupt employees.
- Provide information to auditors proving that devices in your organization are compliant.
- Gather information about device uptime to leverage when diagnosing issues.
- Allow Security and DevOps Teams to interrogate machines to look for security vulnerabilities.
- See which devices are protected by disk encryption and which need to be updated.
Enabling System Insights
Prerequisites:
- System Insights is included in some of our package plans. See JumpCloud Pricing for information on our package plans.
- To enable System Insights for your account, current customers can contact [email protected]. New customers can contact [email protected].
- System Insights only supports 64-bit operating systems.
To automatically enable System Insights for new devices:
- Under Settings > Features, toggle System Insightson or off.
- Under Auto enable System Insights on new devices, select which devices you’d like to enable this feature. Newly added devices will automatically have System Insights enabled.
Devices that existed in your account prior to turning on auto-enablement require that you manually enable System Insights for an individual device.
- Click Save if these are your only changes.
There are two ways to enable System Insights for an individual device:
From the device page:
- Under DEVICE MANAGEMENT > Devices, select a device to view its details.
- On the Insights tab, if System Insights are Disabled an informational block will prompt you to Enable on Device.
- Click Save Device.
From the more actions menu:
- Select a single device from the list view.
- Click more actions, and choose Enable System Insights.
- You are prompted to confirm your selection. Click enable.
To enable System Insights for multiple devices:
- Under DEVICE MANAGEMENT > Devices, select multiple devices by clicking the checkbox for each appropriate device.
- Click more actions, then select Enable System Insights.
To re-enable System Insights after previously disabling System Insights for your organization:
- Under Settings, toggle System Insights to on.
- You are prompted to confirm your selection. Click ok.
Data That System Insights Collects
System Insights collects the following data from your systems.
Every request for system insights data reports the collection_time, which is the timestamp the data was collected from the system. Data is collected every hour. Offline systems report the last known state when they went offline.
This includes vital information about:
- Users and groups
- Hardware and disk utilization
- Applications and browser extensions
- Encryption settings and software versioning
See JumpCloud’s API for all of the endpoints.
Data Categories
The following table describes the data categories System Insights gathers by system.
SI Data Categories
| System Insights Category | Windows | Mac | Linux |
|---|---|---|---|
| System Info and Hardware |
|
|
|
| Operating System |
|
|
|
| Software |
|
|
|
| Network |
|
|
|
| Users and Groups |
|
|
|
Data
The following table describes the specific data System Insights gathers by system.
Data available as of June 23, 2020:
- /systeminsights/authorized_keys
- /systeminsights/appcompat_shims
- /systeminsights/dns_resolvers
- /systeminsights/wifi_networks
- /systeminsights/wifi_status
- /systeminsights/connectivity
- /systeminsights/windows_security_products
- /systeminsights/alf_exceptions
- /systeminsights/alf_explicit_auths
SI Data
| Name | Description | OS Support |
|---|---|---|
| ALF | Returns the OS X Application Layer Firewall (ALF) service details. | Mac |
| ALF Exceptions |
Returns Application Layer Firewall (ALF) service exceptions. You can access it from the 2.0 /systeminsights/alf_exceptions endpoint. Data only available in the API. |
Mac |
| ALF Explicit Auths |
Returns Application Layer Firewall (ALF) services explicity allowed to perform networking. You can access it from the 2.0 /systeminsights/alf_explicit_auths endpoint. Data only available in the API. |
Mac |
| Application Compatibility Shims |
Returns Application Compatibility Shim information from the registry. You can access it from the 2.0 /systeminsights/appcompat_shims endpoint. Data only available in the API. |
Windows |
| Applications | Returns the OS X applications installed in known search paths, such as /Applications. | Mac |
| Authorized Keys |
Returns the authorized_keys table. You can access it from the 2.0 /systeminsights/authorized_keys endpoint. Data only available in the API. |
Linux, Mac |
| Connectivity |
Returns the Windows system's network state. You can access it from the 2.0 /systeminsights/connectivity endpoint. Data only available in the API. |
Windows |
| Battery | Provides information about a MacBook's internal library. Data only available in the API. | Mac |
| BitLocker Info | Returns BitLocker status. | Windows |
| Browser Plugins | Returns all C/NPAPI browser plugin details for all users. | Mac |
| Certificates |
Returns all the Certificate Authorities installed in Keychains/ca-bundles. This table isn't currently available in our API documentation. You can access it from the 2.0 /systeminsights/certificates endpoint. |
Mac, Windows |
| Chrome Extensions | Returns the Chrome browser extension. | Linux, Mac, Windows |
| Crashes | Returns Application, System, and Mobile App crash logs. | Mac |
| CUPS Destination |
Returns all configured printers. This table isn't currently available in our API documentation. You can access it from the 2.0 /systeminsights/cups_destination endpoint. Data only available in the API. |
Mac |
| Disk Encryptions | Returns the disk encryption status and information. | Linux, Mac |
| Disk Info | Returns basic information about a system's physical disks. Data only available in the API. | Windows |
| DNS Resolvers |
Returns DNS resolvers used by the host. You can access it from the 2.0 /systeminsights/dns_resolvers endpoint. Data only available in the API. |
Linux, Mac |
| /etc/hosts | Returns a line-parsed /etc/hosts. | Linux, Mac, Windows |
| Firefox Add-ons | Returns Firefox browser extensions, webapps, and addons. | Linux, Mac |
| Groups | Returns the local system group. Data only available in the API. | Linux, Mac, Windows |
| IE Extensions | Returns Internet Explorer browser extensions for Windows. Data only available in the API. | Windows |
| Interface Addresses | Returns network interfaces and relevant data. | Linux, Mac, Windows |
| Interface Details |
Returns detailed information and stats of network interfaces. This table isn't currently available in our API documentation. You can access it from the 2.0 /systeminsights/interface_details endpoint. |
Linux, Mac, Windows |
| Kernel Info | Returns basic active kernel information. | Linux, Mac, Windows |
| Launchd | Returns the LaunchAgents and LaunchDaemons from default search paths. | Mac |
| Logical Drives | Returns details for logical drives on the system. A logical drive generally represents a single partition. | Windows |
| Logged In Users | Returns users with an active shell on the system. Data only available in the API. | Linux, Mac, Windows |
| Managed Policies | Returns the managed configuration policies from AD, MDM, MCX, and more. Data only available in the API. | Mac |
| Mounts | Returns the system mounted devices and file systems. | Linux, Mac |
| OS Version | Returns the operating system version name and version. | Linux, Mac, Windows |
| Patches | Returns all the patches applied. Doesn't include patches via MSI or that are downloaded from Windows Update Service Packs. | Windows |
| Programs | Returns programs installed by Windows Installer. Some fields may be blank. | Windows |
| Packages | Returns installed deb and rpm packages, version, release or revision, maintainer or vendor, and install date. | Linux |
| Python Packages |
Returns the Python packages installed in a system. Currently, only Python 2 is supported. This table isn't currently available in our API documentation. You can access it from the 2.0 /systeminsights/python_packages endpoint. Data only available in the API. |
Linux, Mac, Windows |
| Safari Extensions | Returns Safari browser extensions. Currently, macOS Mohave and Catalina aren't supported. | Mac |
| Scheduled Tasks |
Returns all of the tasks in the Windows Task Scheduler. This table isn't currently available in our API documentation. You can access it from the 2.0 /systeminsights/scheduled_tasks endpoint. |
Windows |
| Services |
Returns all installed Windows services their and relevant data. This table isn't currently available in our API documentation. You can access it from the 2.0 /systeminsights/services endpoint. |
Windows |
| Shadow | Returns meta information about local system user encrypted passwords. | Linux |
| Shared Resources | Returns the shared resources on a computer system running Windows. Can be a disk drive, printer, interprocess communication, or other shareable device. | Windows |
| Sharing Preferences | Returns OS X sharing preferences. | Mac |
| SIP Configuration | Returns Apple's System Integrity Protection (rootless) status. | Mac |
| Startup Items |
Returns applications and binaries set as user/login startup items. This table isn't currently available in our API documentation. You can access it from the 2.0 /systeminsights/startup_items endpoint. |
Mac, Windows |
| System Controls | Returns the system information for identification. | Linux, Mac, Windows |
| System Info | Returns the system information for identification. | Linux, Mac, Windows |
| Uptime | Returns the time passed since last boot. | Linux, Mac, Windows |
| USB Devices | Returns USB devices that are actively plugged in to the host system. Data only available in the API. | Linux, Mac |
| User Groups | Returns the local system user group relationships. | Linux, Mac, Windows |
| Users | Returns the list of local user accounts. Data only available in the API. | Linux, Mac, Windows |
| User SSH Keys | Returns the encrypted state for private keys in the user's ~/.ssh directory. | Linux, Mac |
| WiFi Networks |
Returns the known and remembered WiFi networks. You can access it from the 2.0 /systeminsights/wifi_networks endpoint. Data only available in the API. |
Mac |
| WiFi Status |
Returns the Mac WiFi status. You can access it from the 2.0 /systeminsights/wifi_status endpoint. Data only available in the API. |
Mac |
| Windows Security Products |
Returns the registered Windows security products. You can access it from the 2.0 /systeminsights/windows_security_products endpoint. Data only available in the API. |
Windows |
Using and Viewing System Insights Data
After you’ve enabled System Insights for your organization's devices, you can use the JumpCloud API and the JumpCloud PowerShell module to query and report on System Insights information.
Prerequisites:
- System Insights must be enabled on a device for the System Insights section to appear under the Device panel Details tab.
To view System Insights data for a device:
- Go to Devices.
- Select a device that has System Insights enabled, and select the Insights tab.
- From here, sub-tabs provide extra navigation.
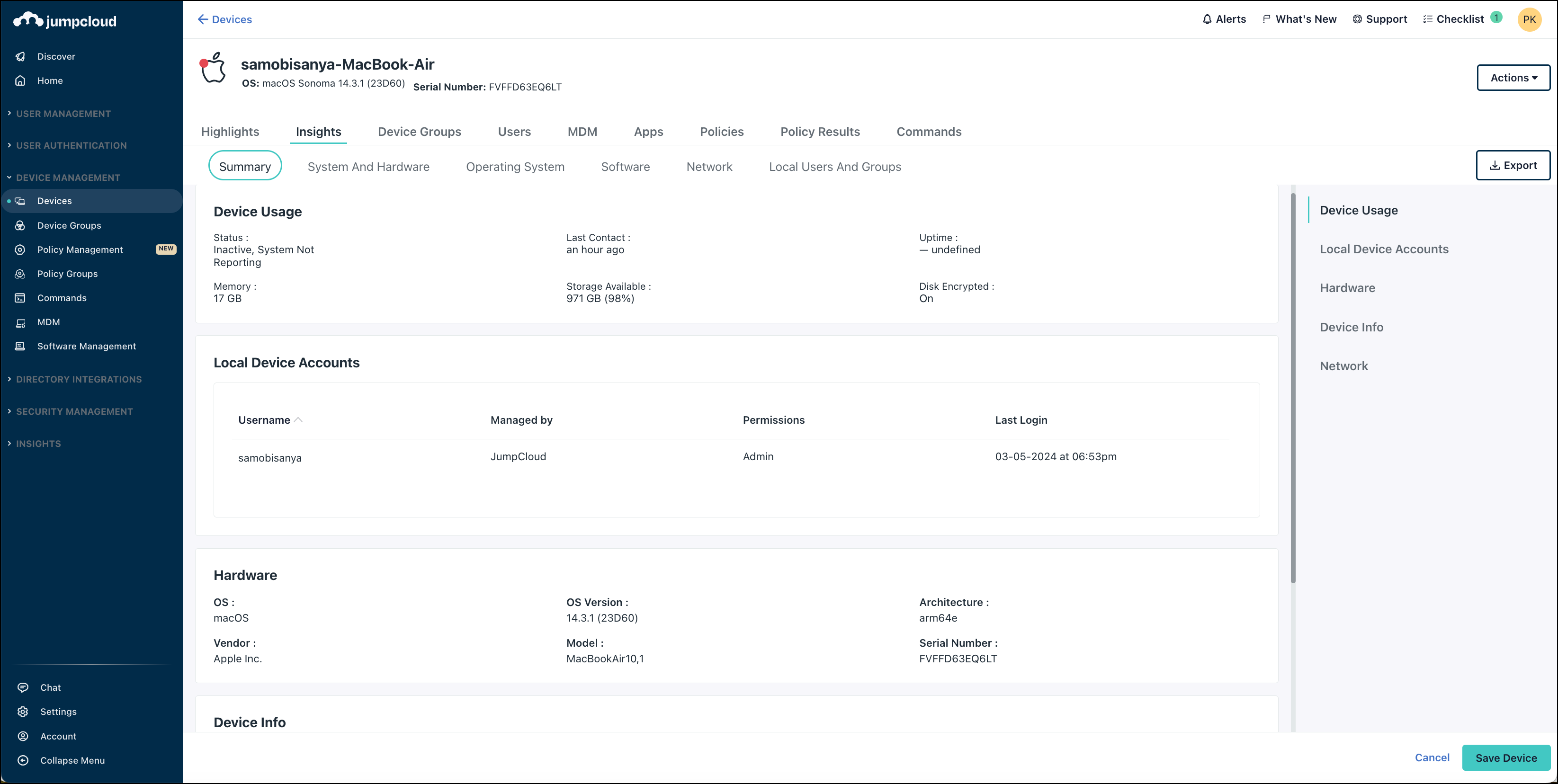
The Summary tab shows the following data:
- Device Usage
- Status: active or inactive
- Last Contact: last activity from the device
- Uptime: The number of days since the device was last rebooted.
- Memory: The amount of RAM or memory installed on the device.
- Storage Available: The amount of storage space available in the device’s largest partition.
- Disk Encrypted: Whether disk encryption (BitLocker, FileVault, or Linux Encryption) is enabled for the device.
- Local Device Accounts
- Hardware: Information on the device hardware, such as operating system version, architecture, vendor, model, and serial number.
- Device Info: Information from the agent, such as Instance ID, System ID, and agent version.
- Network: Information on the hostname, primary, and remote IP addresses.
Retainment of System Insights Data
JumpCloud retains System Insights data as long as the device exists within the Admin Portal. When the device is deleted, System Insights data transmission is automatically terminated for that device.
System Insights collects a single copy of data every 60 minutes, meaning that the data is not live, and is refreshed every hour. For longer data retention, if needed by your org, we recommend migrating the data out of System Insights via JumpCloud's System Insights API to a storage space like AWS S3 Bucket or Azure Blob.
See our API docs or more information.