The configuration settings were tested on the latest version as of 06/09/2021.
Prerequisites:
- See Use Cloud LDAP to obtain the JumpCloud specific settings required below.
Okta LDAP Agent Configuration
When using the Okta LDAP Agent, here are the basic settings to configure authentication with JumpCloud's hosted LDAP service:
- LDAP Server: ldap.jumpcloud.com
- Root DN: ou=Users,o=YOUR_ORG_ID,dc=jumpcloud,dc=com
- Bind DN: uid=LDAP_BIND_USER,ou=Users,o=YOUR_ORG_ID,dc=jumpcloud,dc=com
- Bind Password: LDAP_BIND_USER_PASSWORD
- Use SSL connection: Enable for SSL
LDAP Configuration Settings in Okta
Version
- LDAP Version: OpenLDAP
Objects
- Unique Identifier Attribute: entrydn
- DN Attribute: entrydn
Users
- User Search Base: ou=Users,o=YOUR_ORG_ID,dc=jumpcloud,dc=com
- User Object Class: inetorgperson
- User Object Filter: (objectclass=inetorgperson)
- Account Disabled Attribute: pwdlock
- Account Disabled Value: true
- Password Attribute: userpassword
Group
- Group Search Base: ou=Users,o=YOUR_ORG_ID,dc=jumpcloud,dc=com
- Group Object Class: groupofnames
- Group Object Filter: (objectclass=groupofnames)
- Member Attribute: member
- User Attribute: memberof
Role
- Object Class: groupofnames
- Membership Attribute: memberof
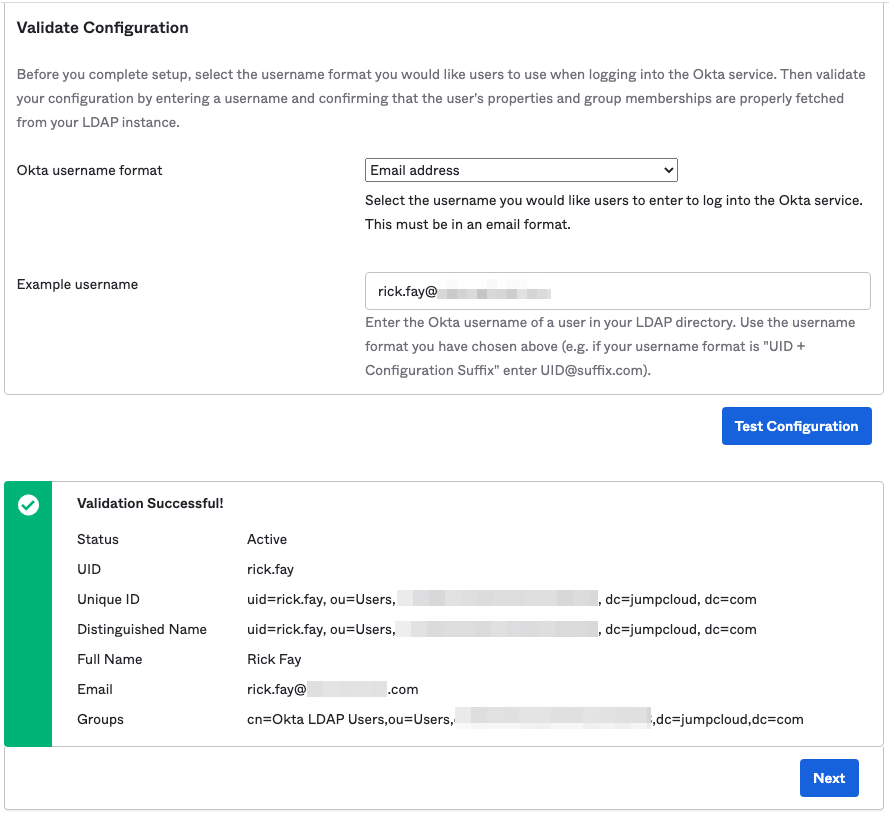
Validating Configurations
- Okta username format: email
- Example username: [email protected]
Use any email address associated to a user's JumpCloud account. The User in JumpCloud must also be bound either directly to or a member of a User Group which has been bound to LDAP. This will test to see if Okta can query an existing JumpCloud user through the Okta LDAP Agent to JumpCloud.
Example of a Successfully Validated Configuration
Importing Users into Okta from JumpCloud via LDAP
Once you've configured Okta LDAP's Directory Integration and LDAP Agents, the next step is to import Users from JumpCloud.
To import users into Okta from JumpCloud:
- Navigate to Directory Integrations and select the newly configured LDAP Directory Integration you’ve just configured in the steps above.
- Select the Import tab.
- Click Import Now.
- A pop up modal will appear, allowing you to select Incremental or Full. This will be based on how you would like to import users. To start or test the import, select Incremental.
- Click Import.
- You’ll see the number of Users and Groups that have been scanned from your JumpCloud organization that have been bound to JumpCloud LDAP.
- You can then select the users you’d like to import into Okta from JumpCloud from this list.
- When you’re ready to import these selected users, select Confirm Assignments.
Once you've imported your users from JumpCloud into Okta via LDAP, you should see these Users within the People tab within the Okta LDAP Directory Integration within Okta's admin portal.
Troubleshooting
If the error Could not find a value for the BaseSubstitutionProperty on the User result is received, perform the following steps to resolve:
- During initial configuration, remove the
memberOfvalue for the Groups > User Attribute configuration and leave the field blank. - After the configuration is successfully saved, this value may then be re-input as per the configuration listed below.
- If the verification test continues to fail after replacing the memberOf attribute within the configuration, then confirm that your LDAP Users have been associated with an LDAP-enabled group as the query performed by Okta requires the attribute to be present in the user object during the verification.