Google Cloud Directory Sync (GCDS) makes it possible for Google accounts to sync with Microsoft’s Active Directory (AD). It’s a core component of Google’s approach to identity and access management (IAM), which is to provide IT admins with as much optionality as possible.
This article explores why integrating Google with AD is beneficial and other ways IT admins can leverage Google and its partner ecosystem to modernize their IT infrastructure. JumpCloud has partnered with Google to help small and medium-sized enterprises (SMEs) to extend or replace Active Directory or to enable other important use cases such as migrating from on-premises Exchange to Google Workspace. Broader customer choice is a major benefit of Google IAM over using Microsoft’s ecosystem for single sign-on (SSO) and cloud directory synchronization.
GCDS and Active Directory
GCDS is the identity bridge between Active Directory and Google Workspace’s account directory. Its utility is installed on Windows Server on premises (or in Google Cloud) and configured to sync Active Directory’s users, aliases, groups, and other data with Google. It communicates over port 443 HTTPS/SSL and uses Google’s Virtual Private Cloud (VPC) access connector to establish a secure network connection with Google’s Cloud Identity. Google Cloud Identity handles user and access management for Google resources, and more.
Changes that are in AD are reflected to GCDS and subsequently to Google’s identity management platform in the cloud. Active Directory is the authoritative source of identity. For example, suspended or deleted AD users will also be disabled in Google Cloud Identity.
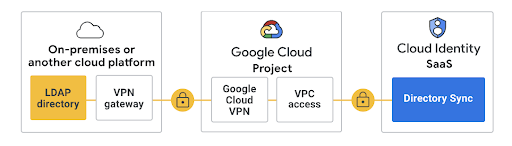
This configuration will make it possible to adopt Google Workspace while keeping AD as your identity provider (IdP).
Active Directory Doesn’t Meet Modern Requirements
However, many IT organizations are shifting away from Active Directory. This is largely due to the fact that AD no longer provides IT organizations with efficient and effective user management across all endpoints and locations. Security is also motivating this change. Implementing AD according to its best practices is challenging and can become expensive. It also requires point solutions (or Microsoft subscriptions) to function as a modern directory.
Specifically, AD doesn’t provide these essential features:
- Advanced lifecycle management to protect your resources through mature entitlement management.
- Unified endpoint management (UEM) to ensure that every endpoint that accesses your resources meets a minimal threshold for compliance and security.
- SSO to everything with environment-wide multi-factor authentication (MFA), including common network protocols.
- No modern authentication or conditional access to increase security.
Then, there’s the security considerations. A recent report found, “Approximately 95 million Active Directory accounts are attacked daily, as 90% of organizations use the identity platform as their primary method of authentication and user authorization.” SMEs are at particular risk if they haven’t taken steps to implement a cybersecurity program and lower AD’s attack surface. Windows admins don’t need to be reminded about the disruptions caused by zero-day exploits.
These issues are concerning, but migrations may seem difficult. Some SMEs within regulated industries may require on-premises authentication, while others can consider more modern alternatives. Google offers pathways for both scenarios, either standalone or with JumpCloud. Migrating away from AD (or extending it to do more) isn’t all or nothing or unapproachable.
Google’s IAM Pathway
Google Cloud Identity offers free and premium editions with the primary difference being app management, device management, and other advanced features that aren’t available for free. Google recommends JumpCloud for SMEs that are extending or migrating off of AD.
JumpCloud and Google are complementary. Both platforms use dynamic groups that use user attributes to automate memberships. JumpCloud imports users into groups from Microsoft, Google, Okta, and HR systems. JumpCloud’s groups logically separate objects in a manner that’s simpler than managing OUs within AD, while providing stronger lifecycle management.
This open directory platform helps SMEs extend or discontinue using Active Directory with unified endpoint and identity management to deliver essential endpoint compliance and security capabilities. Here’s a brief overview of JumpCloud’s features that are helpful for SMEs.
JumpCloud for SMEs Using AD
JumpCloud’s open directory platform provides centralized IAM and unified endpoint management, regardless of the underlying authentication method or device ecosystem. For instance, it can integrate with and migrate users off of AD. Organizations can move to its cloud directory at their own discretion or extend AD by managing non-Windows devices.
JumpCloud ensures that every resource has a “best way” to connect to it with authentication methods including biometrics, certificates, passwordless workflows, or SSH keys. A phishing-resistant modern authentication is also coming soon. The platform includes lifecycle management, remote assistance, and commands to run remediations across your endpoints.
- Conditional access is available to reduce sign-in risk.
- JumpCloud supports web protocols including SAML, OIDC, and SCIM provisioning. It provides common networking protocols such as LDAP and RADIUS.
- IT management options include cross-OS patch management and a password manager that blends a secure, decentralized architecture with security controls and visibility.
Unifying cross-domain identity and device management with JumpCloud can reduce costs for IT, improve operational efficiencies, strengthen cybersecurity, support workplace and identity transformation, and reduce the pressure on your IT admins and security teams.
Many IT admins are leaving self-hosted email behind to increase security. Exchange zero-days are being used in attacks.
Migrating Off of Exchange
JumpCloud blazes a migration path away from on-premises Exchange to Google Workspace to increase security, reduce managerial overhead, and move toward a modern, scalable infrastructure. That’s significant for SMEs that find themselves tethered to Exchange, because Exchange has double to almost triple the security incident risk than Google Workspace, according to a recent report from cyber insurance broker At-Bay. Google was the top-performing email solution in its findings with 40% fewer security incidents than other email providers.
Google and JumpCloud are better together, and offer IT admins a path toward modernization.
Find Out More
Get started with GCDS or consider signing up for a free trial of JumpCloud if unified endpoint and identity management is a better option for you. Active Directory integration is included at no additional cost, along with UEM and SSO to securely connect to your resources.




